 By Joseph Cox
By Joseph Cox
Hackers are able to grab a target’s IP address, potentially revealing their general physical location, by simply sending a link over the Skype mobile app. The target does not need to click the link or otherwise interact with the hacker beyond opening the message, according to a security researcher who demonstrated the issue and successfully discovered my IP address by using it.
Yossi, the independent security researcher who uncovered the vulnerability, reported the issue to Microsoft earlier this month, according to Yossi and a cache of emails and bug reports he shared with 404 Media. In those emails Microsoft said the issue does not require immediate servicing, and gave no indication that it plans to fix the security hole. Only after 404 Media contacted Microsoft for comment did the company say it would patch the issue in an upcoming update.
The attack could pose a serious risk to activists, political dissidents, journalists, those targeted by cybercriminals, and many more people. At minimum, an IP address can show what area of a city someone is in. An IP address can be even more revealing in a less densely populated area, because there are fewer people who could be associated with it.
“I think just about anybody could be harmed by this,” Cooper Quintin, a security researcher and senior public interest technologist at activist organization the Electronic Frontier Foundation (EFF), said when I explained the issue to him. Quintin said the major concern was “finding people’s location for physical escalations, and finding people’s IP address for digital escalations.”
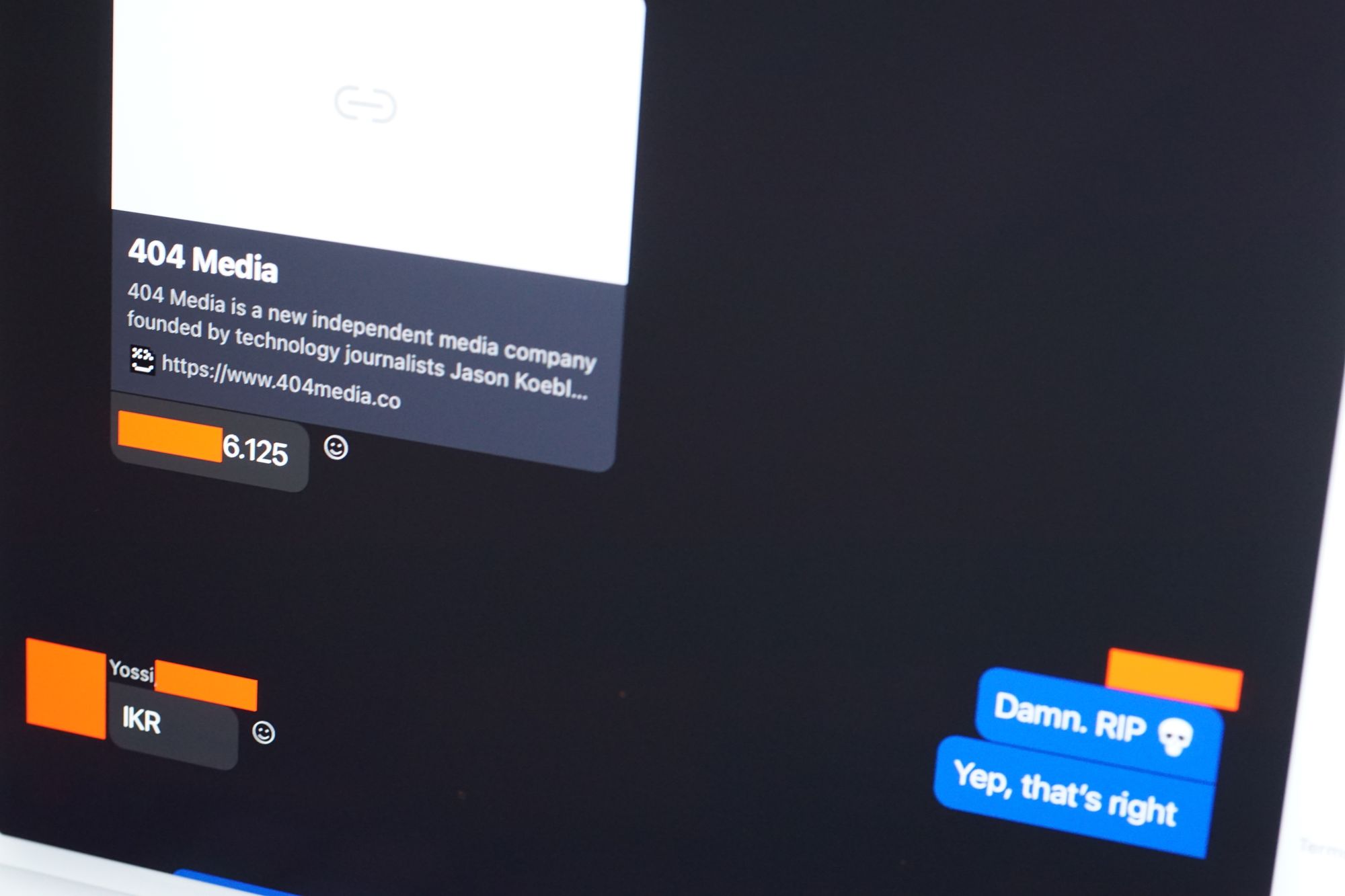
To verify that the vulnerability has the impact that Yossi described, I asked him to test it out on me. To start, Yossi sent me a link via Skype text chat to google.com. The link was to the real Google site, and not an imposter.
I then opened Skype on an iPad and viewed the chat message. I didn’t even click the link. But very soon after, Yossi pasted my IP address into the chat. It was correct.
For that first test, I connected to Skype using a virtual private network, which can protect you from others learning your home or office IP address. I wanted to double check the potential for abuse with this vulnerability, so I then connected to a public wifi network without a VPN and asked Yossi to send another link. This time, he sent a link to 404media.co. Like the earlier test, the link itself was legitimate and not spoofed.
Once again, Yossi found my current IP address. This time, it pointed to the area of the city I was speaking to him from.
“Damn, RIP 💀,” I wrote in response.
The issue only applies to Skype’s mobile apps, Yossi said. When I used the Mac version of Skype, he was unable to learn my IP address.
Generally speaking, when people chat over an app or other service, the app not only facilitates that communication but also acts as something of a buffer between them. In many cases the service—in this instance, Skype—will know each individual user’s IP address simply by virtue of how the internet works. For a service to mask that information from itself, it may need to make additional, privacy-focused engineering decisions. But even if the service does know each person’s IP address, it doesn’t usually share the information between the two people speaking.
Skype, however, does share that info between the people speaking, at least when one of them knows how to exploit a certain security hole. Skype is allowing a hacker to reach out and grab their target’s IP address without the victim’s knowledge or consent. Quintin pointed to the potential of abuse against dissidents who operate under pseudonyms. This attack could be used to learn their physical location and identity.
When Yossi reported the issue to Microsoft, the company said on August 12th that the “disclosure of an IP address is not considered a security vulnerability on it’s [sic] own,” according to a copy of the email Yossi shared. Yossi then explained that exposure of an IP address could invade someone’s privacy, lead to abuse by a jealous partner; or lead to more invasiveness cyberattacks too.
“Upon investigation, we have determined that this submission does not meet the definition of a security vulnerability for servicing which would require immediate servicing. This report does not appear to identify a weakness in a Microsoft product or service that would enable an attacker to compromise the integrity, availability, or confidentiality of a Microsoft offering,” Microsoft responded.
Only after 404 Media contacted Microsoft for comment did the company say it planned to fix the issue in an upcoming patch.
“We appreciate the work of this security researcher in identifying and responsibly reporting their findings. We have determined that this report does not meet the bar for immediate servicing under our severity classification guidelines based on the exposure of an IP address alone; however, we will be addressing it in a future product update as a defense in depth improvement to help keep customers protected,” a Microsoft spokesperson said in an email. The spokesperson gave no timeline for when users could expect this update, but added that this vulnerability does not impact Skype’s business product.
Because Microsoft has not fixed it, 404 Media is not explaining the specifics of the vulnerability in great detail. But it is trivially easy to exploit and involves changing a certain parameter related to the link.
The vulnerability remains. As of Monday, the issue was still replicable.
“I’m very dismayed that Skype won’t take this seriously,” Quintin added. “I think this is emblematic of why Skype has lost so much market share.”
Source: 404 Media
404 Media is a new independent media company founded by technology journalists Jason Koebler, Emanuel Maiberg, Samantha Cole, and Joseph Cox. Become a paid subscriber HERE
Do you know about any other vulnerarbilities a company is refusing to fix? I would love to hear from you. Using a non-work device, you can message me securely on Signal at +44 20 8133 5190. Otherwise, send me an email at joseph@404media.co.
Image: The IP-grabbing vulnerability in action. Image: Jason Koebler
Become a Patron!
Or support us at SubscribeStar
Donate cryptocurrency HERE
Subscribe to Activist Post for truth, peace, and freedom news. Follow us on SoMee, Telegram, HIVE, Flote, Minds, MeWe, Twitter, Gab, and What Really Happened.
Provide, Protect and Profit from what’s coming! Get a free issue of Counter Markets today.

Be the first to comment on "Hackers Can Silently Grab Your IP Through Skype — Microsoft Is In No Rush to Fix It"