 By B.N. Frank
By B.N. Frank
Tesla vehicles continue to be associated with all kinds of undesirable safety (see 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19) and security issues (see 1, 2). Recently, a researcher made a video that demonstrates how a Tesla update made it even easier to steal these cars.
From Ars Technica:
Gone in 130 seconds: New Tesla hack gives thieves their own personal key
You may want to think twice before giving the parking attendant your Tesla-issued NFC card.
Sometime last year, Tesla issued an update that made its vehicles easier to start after being unlocked with their NFC Key Cards. Now, a researcher has shown how the feature can be exploited to steal cars.
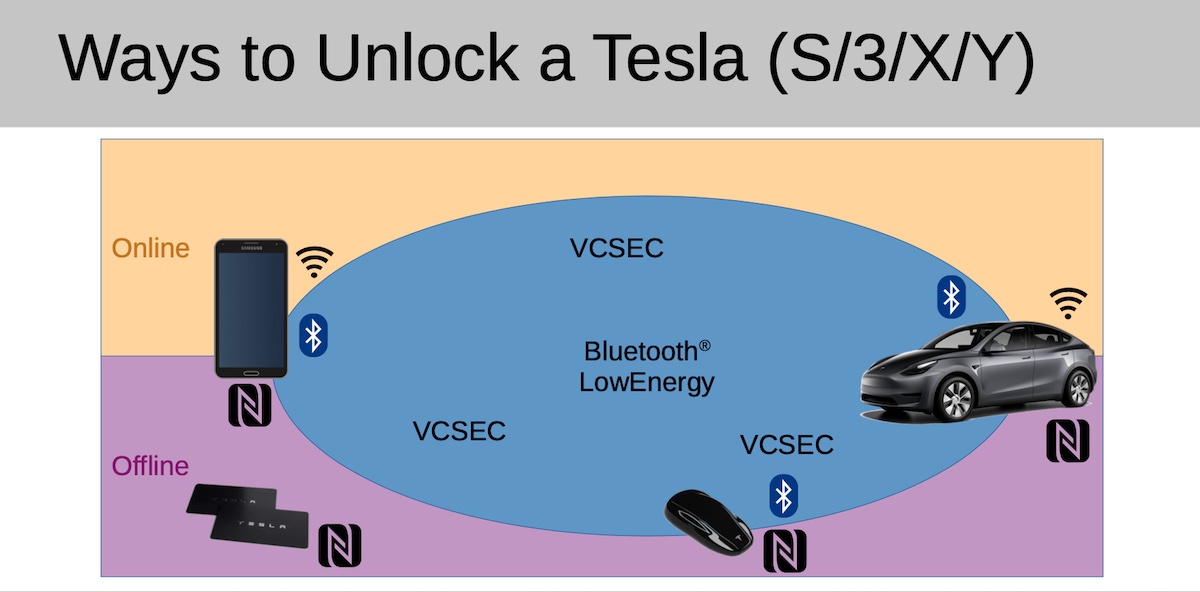
For years, drivers who used their Tesla NFC Key Card to unlock their cars had to place the card on the center console to begin driving. Following the update, which was reported here last August, drivers could operate their cars immediately after unlocking them with the card. The NFC card is one of three means for unlocking a Tesla; a key fob and a phone app are the other two.
Enrolling your own key
Martin Herfurt, a security researcher in Austria, quickly noticed something odd about the new feature: Not only did it allow the car to automatically start within 130 seconds after being unlocked with the NFC card, but it also put the car in a state to accept entirely new keys—with no authentication required and zero indication given by the in-car display.
“The authorization given in the 130-second interval is too general… [it’s] not only for drive,” Herfurt said in an online interview. “This timer has been introduced by Tesla … in order to make the use of the NFC card as a primary means of using the car, more convenient. What should happen is that the car can be started and driven without the user having to use the keycard a second time. The problem: within the 130-second period, not only the driving of the car is authorized, but also the [enrolling] of a new key.”
The official Tesla phone app doesn’t permit keys to be enrolled unless it’s connected to the right owner’s account, but despite this, Herfurt found that the vehicle gladly exchanges messages with any Bluetooth Low Energy, or BLE, device that’s nearby. So the researcher built his own app, named Teslakee, that speaks VCSec, the same language that the official Tesla app uses to communicate with Tesla cars.
A malicious version of Teslakee that Herfurt designed for proof-of-concept purposes shows how easy it is for thieves to surreptitiously enroll their own key during the 130-second interval. (The researcher plans to release a benign version of Teslakee eventually that will make such attacks harder to carry out.) The attacker then uses the Teslakee app to exchange VCSec messages that enroll the new key.
All that’s required is to be within range of the car during the crucial 130-second window of it being unlocked with an NFC card. In the event a vehicle owner normally uses the phone app to unlock the car—by far the most common unlocking method for Teslas—the attacker can force the use of the NFC card by using a signal jammer to block the BLE frequency used by Tesla’s phone-as-a-key app.
This video demonstrates the attack in action:
As the driver enters the car after unlocking it with her NFC card, the thief begins exchanging messages between the weaponized Teslakee and the car. Before she has even driven away, the messages enroll a key of the thief’s choice with the car. From then on, the thief can use the key to unlock, start, and turn off the car. There is no indication from the in-car display or the legitimate Tesla app that anything is amiss.
Herfurt has successfully used the attack on Tesla Models 3 and Y. He hasn’t tested the method on new 2021+ facelift models of the S and X, but he presumes they are also vulnerable because they use the same native support for phone-as-a-key with BLE.
Tesla didn’t respond to an email seeking comment for this post.
Parlez-vous VCSec?
The vulnerability is the result of the dual roles played by the NFC card. Not only does it open a locked car and start it, it is also used to authorize key management. Herfurt said that the attack:
exploits Tesla’s way of handling the unlock process via NFC-Card. This works because Tesla’s authorization method is broken. There is no connection between the online account world and the offline BLE world. Any attacker who can see the Bluetooth LE advertisements of a vehicle may send VCSEC messages to it. This would not work with the official app, [but] an app that is also able to speak the tesla-specific BLE protocol … allows attackers to enroll keys for arbitrary vehicles. Teslakee will communicate with any vehicle if it is told to.
Herfurt created TeslaKee as part of Project Tempa, which “provides tools and information about the VCSEC protocol used by Tesla accessories and the Tesla app in order to control vehicles via Bluetooth LE.” Herfurt is a member of Trifinite Group, a research and hacker collective that focuses on BLE.
The attack is easy enough in technical aspects to carry out, but the mechanics of staking out an unattended vehicle, waiting for or forcing the owner to unlock it with an NFC card, and later catching up with the car and stealing it can be cumbersome. This method isn’t likely to be practical in many theft scenarios, but for some, it seems viable.
With Tesla maintaining radio silence on this weakness, there’s only so much concerned owners can do. One countermeasure is to set up Pin2Drive to prevent thieves who use this method from starting a vehicle, but it will do nothing to prevent the thief from being able to enter the car when it’s locked. Another protection is to regularly check the list of keys authorized to unlock and start the car through a process Tesla calls “whitelisting.” Tesla owners may want to perform this check after giving an NFC card to an untrusted mechanic or valet parking attendant.
Based on the lack of response Herfurt said he received from Tesla on vulnerabilities he uncovered in 2019 and again last year, he’s not holding his breath.
“My impression was that they always already knew and would not really change stuff,” he said. “This time there is no way that Tesla does not know about that poor implementation. So for me, there was no point in talking to Tesla beforehand.”
Teslas have also been associated with battery fires, fires that are difficult to extinguish, and high levels of harmful radiation emissions (see 1, 2, 3). Of course, battery fires, fires that are difficult to extinguish, and high levels of harmful radiation emissions have been reported with other company’s electric vehicles (EVs) as well (see 1, 2, 3, 4).
Activist Post reports regularly about Teslas, autonomous vehicles (AVs), EVs, and unsafe technology. For more information, visit our archives and the following websites:
- Wireless Information Network
- Electromagnetic Radiation Safety
- Environmental Health Trust
- Physicians for Safe Technology
Top image: Pixabay
Become a Patron!
Or support us at SubscribeStar
Donate cryptocurrency HERE
Subscribe to Activist Post for truth, peace, and freedom news. Follow us on SoMee, Telegram, HIVE, Flote, Minds, MeWe, Twitter, Gab, What Really Happened and GETTR.
Provide, Protect and Profit from what’s coming! Get a free issue of Counter Markets today.

Be the first to comment on "New Tesla Hack: Car Will “accept entirely new keys—with no authentication required and zero indication given by the in-car display” (Video)"