 By B.N. Frank
By B.N. Frank
Cybersecurity risks and warnings regarding ALL wireless, “Smart”, and Internet of Things (IoT) technology and infrastructure are nothing new. 5G is simply getting more attention. In fact, several federal agencies and numerous experts (see 1, 2) have issued warnings about how it threatens national security, public safety, and even weather forecasting accuracy.
Thanks to Scientists4WiredTech for reporting more on their blog:
Long-standing, Established 3G/4G/5G Equipment Security Flaw
Forget TikTok. Feebly Secured Infrastructure Is Our Real Problem
By Karl Bode, Aug 11, 2020 | Original TechDirt article here.
Long-standing, Established 3G/4G/5G Equipment Security Flaw
Steve Gibson from Security Now | The paper, Impersonation Attacks in 4G/5G Networks, is here: web | pdf
One of the dumber aspects of press coverage of the TikTok kerfuffle is the lack of broader context.
How, exactly, does banning a Chinese-owned teen dancing app solve our security and privacy headaches in a world where apps and services everywhere are collecting most of the same data, if not more? And why the myopic focus on just TikTok when Americans attach millions of totally unsecured Chinese-made “smart” IOT devices to their home and business networks with reckless abandon? If you’re going to freak out about U.S. consumer privacy and internet security — why not focus on actually shoring up overall U.S. consumer privacy and security?
Many press outlets and analysts have innately bought into the idea that banning TikTok somehow seriously thwarts the Chinese government’s spying efforts. In reality, China’s spying capabilities, fueled by an unlimited budget, have no limit of potential other ways to get far more data thanks to United States’ lax privacy and security standards. Case in point, last week in the midst of TikTok hysteria, a report quietly emerged showing that the U.S. satellite communications networks have the security of damp cardboard:
“More than a decade has passed since researchers demonstrated serious privacy and security holes in satellite-based Internet services. The weaknesses allowed attackers to snoop on and sometimes tamper with data received by millions of users thousands of miles away. You might expect that in 2020—as satellite Internet has grown more popular—providers would have fixed those shortcomings, but you’d be wrong.”
The security researcher in question showcased how it wasn’t particularly difficult to hack into these satellite networks to observe all manner of online activity, from airliners receiving unencrypted navigation data in flight, to utility administrators managing wind turbines. Many of these vulnerabilities have been known about for fifteen years yet still haven’t been fixed:
“There are still many satellite Internet services operating today which are vulnerable to their [the previous researchers’] exact attacks and methods — despite these attacks having been public knowledge for more than 15 years at this point,” Pavur told me ahead of Wednesday’s talk. “We also found that some newer types of satellite broadband had issues with eavesdropping vulnerabilities as well.”
Which is all to say: if you’re going to freak out about TikTok, why not at least spend some of those calories discussing actually trying to fix our broader cybersecurity and privacy problems? Why not create systems that are simply resilient, transparent, and accountable by design?
- The U.S. still doesn’t have even a basic privacy law for the internet era,
- companies routinely face no serious penalty for privacy missteps,
- our privacy regulators are routinely kneecapped and under-funded,
- consumer data is routinely left open on the cloud,
- a new hack is revealed at least once a week, and
- nobody wants to spend the funds necessary to upgrade older infrastructure because doing so simply isn’t sexy.
To ignore this and then become utterly hysterical because the Chinese government might get some teen phone data, is utter nonsense. Yet most of main stream media coverage of the dangers of TikTok have has lacked the context of this broader reality.
- The mainstream media were nowhere to be found among efforts to fix a massive SS7 flaw that makes our cellular infrastructure vulnerable.
- The mainstream media were dead quiet as folks tried to hold the cellular industry accountable for selling everybody’s location data to any nitwit with a nickel.
In fact, most of the folks that have hyperventilated the most about TikTok have repeatedly shot down attempts at internet-era privacy laws and fought against funding to secure U.S. elections. Why, it’s almost as if many of them don’t actually care about U.S. privacy and security, and instead are performatively upset about TikTok for xenophobic, financial, and political reasons.
If one is seriously concerned about U.S. cybersecurity and privacy issues, then one must work to actually try to fix those problems instead of engaging in histrionics about a teenage dancing app. It only takes a few hours of reading about the U.S. cybersecurity and privacy incompetence before you come to realize that TikTok is among the very least of this country’s problems on that front.
Exactly Six Months Earlier . . .
SS7 Cellular Network Flaw Nobody Wants To Fix Now Being Exploited To Drain Bank Accounts
By Karl Bode, Feb 11, 2020 | Original TechDirt article here.
Back in 2017, you might recall how hackers and security researchers highlighted long-standing vulnerabilities in Signaling System 7 (SS7, or Common Channel Signalling System 7 in the US), a series of protocols first built in 1975 to help connect phone carriers around the world. While the problem isn’t new, a 2016 60 minutes report brought wider attention to the fact that the flaw can allow a hacker to track user location, dodge encryption, and even record private conversations. All while the intrusion looks like ordinary carrier to carrier chatter among a sea of other, “privileged peering relationships.”
Telecom lobbyists have routinely tried to downplay the flaw after carriers have failed to do enough to stop hackers from exploiting it. In Canada for example, the CBC recently noted how Bell and Rogers weren’t even willing to talk about the flaw after the news outlet published an investigation showing how, using only the number of his mobile phone, it was possible to intercept the calls and movements of Quebec NDP MP Matthew Dubé.
But while major telecom carriers try to downplay the scale of the problem, news reports keep indicating how the flaw is abused far more widely than previously believed. This Motherboard investigation by Joseph Cox, for example, showed how, while the attacks were originally only surmised to be within the reach of intelligence operators (perhaps part of the reason intelligence-tied telcos have been so slow to address the issue), hackers have increasingly been using the flaw to siphon money out of targets’ bank accounts, thus far predominately in Europe:
“In the case of stealing money from bank accounts, a hacker would typically first need a target’s online banking username and password. Perhaps they could obtain this by phishing the target. Then, once logged in, the bank may ask for confirmation of the transfer by sending the account owner a verification code in a text message. With SS7, the hackers can intercept this text and enter it themselves. Exploiting SS7 in this way is a way to circumvent the protections of two-factor authentication, where a system not only requires a password, but something else too, such as an extra code.”
Again the flaw isn’t new; a group of German hackers widely demonstrated the vulnerability in 2008 and again in 2014. It’s believed that the intelligence community has known about the vulnerability even earlier, and the hackers note that only modest headway has been made since German hacker Karsten Nohl first demonstrated it. Some mitigation efforts have been put into place, but not quickly or uniformly enough to constrain the exploitation of the flaw:
“The fundamental issue with the SS7 network is that it does not authenticate who sent a request. So if someone gains access to the network — a government agency, a surveillance company, or a criminal — SS7 will treat their commands to reroute text messages or calls just as legitimately as anyone else’s. There are protections that can be put in place, such as SS7 firewalls, and ways to detect certain attacks, but room for exploitation remains.”
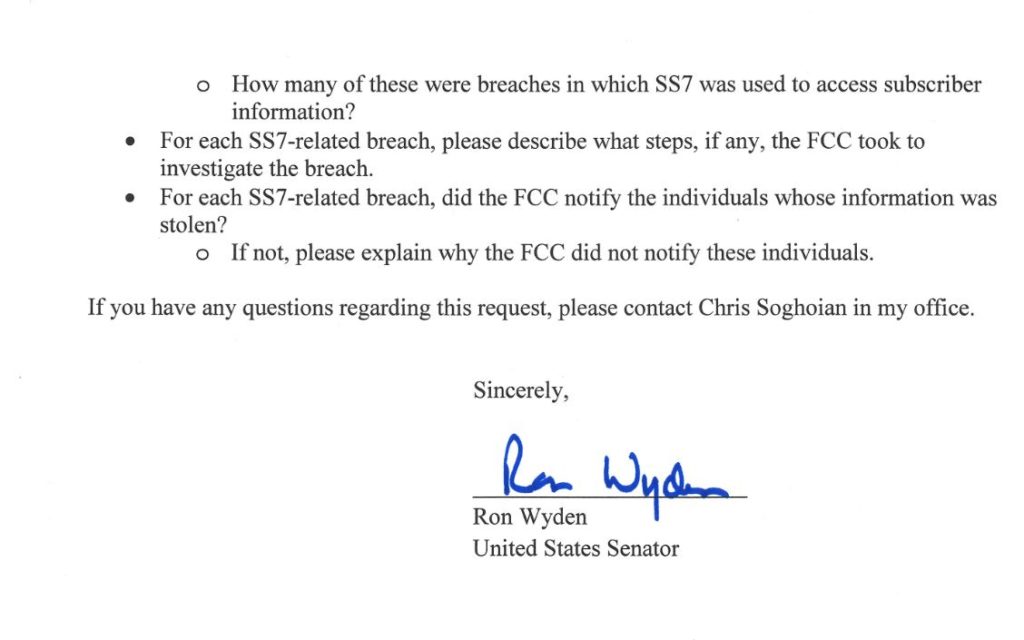
Senator Ron Wyden wrote to the FCC (pdf) in May of last year stating the agency hadn’t done enough to pressure carriers into fixing the problem, but nothing much appears to have happened in the wake of that letter. Much like the cellular industry’s location data scandals, it’s likely going to take a few more high profile scandals to create enough momentum to drive actual change.
In regard to 5G, cities AND entire countries have taken action to ban, delay, halt, and limit installation as well as issue moratoriums due to health and safety risks. The majority of scientists worldwide are opposed to deployment until there studies show that it’s safe. Seems reasonable, doesn’t it.
Activist Post reports regularly about unsafe technology. For more information visit our archives.
Subscribe to Activist Post for truth, peace, and freedom news. Send resources to the front lines of peace and freedom HERE! Follow us on SoMee, HIVE, Parler, Flote, Minds, and Twitter.
Provide, Protect and Profit from what’s coming! Get a free issue of Counter Markets today.



Be the first to comment on "U.S. Cybersecurity Risks Include Way More than TikTok"