On Tuesday morning WikiLeaks released brand new documents related to surveillance operations conducted by the U.S. Central Intelligence Agency.
WikiLeaks has further exposed the Central Intelligence Agency’s spying capabilities in an explosive new document dump dubbed “Vault 7.” The vault is a massive collection of data regarding CIA surveillance activities with documents that detail everything from the CIA’s infiltration of smart phones, televisions, and cars, to the creation of a hacking station posing as a U.S. Consulate in Germany.
The release of the documents was not without controversy, as the electronics of WikiLeaks founder Julian Assange were reportedly “under attack.” A tweet from WikiLeaks states, “the press conference is under attack: Facebook+Periscope video used by WikiLeaks’ editor Julian Assange have been attacked. Activating contingency plans.”
Press conf under attack: Facebook+Periscope video used by WikiLeaks’ editor Julian Assange have been attacked. Activating contingency (1/2)
— WikiLeaks (@wikileaks) March 7, 2017
WikiLeaks claims that the CIA recently lost control over a “majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation”. The archive was apparently circulated among former U.S. government hackers and contractors before being shared with WikiLeaks.
“The first full part of the series, “Year Zero”, comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA’s Center for Cyber Intelligence in Langley, Virgina,” WikiLeaks wrote in a press release. Year Zero focuses on the CIA’s global hacking program, their full arsenal of malware programs, and so-called “Zero Day” exploits for the U.S. and Europe’s most popular computer products, phones, and televisions.
That Samsung smart TV? The CIA can turn the mic on and listen to everything you say #vault7 #1984rebooted pic.twitter.com/CAm1E2TgxV
— WikiLeaks (@wikileaks) March 7, 2017
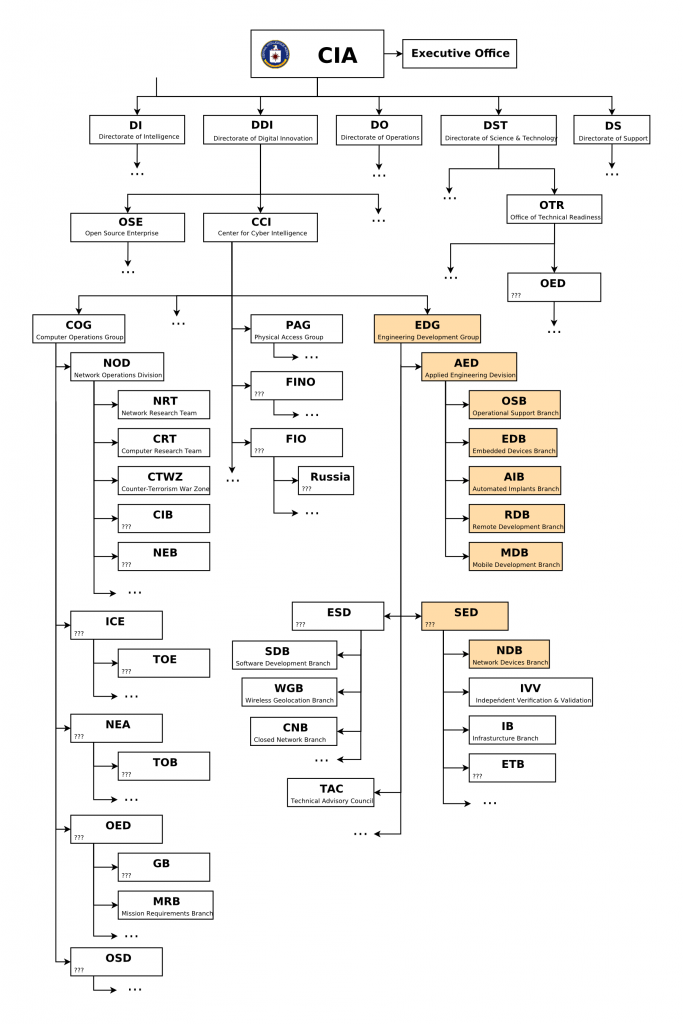
The documents detail how the CIA’s hacking squad had blossomed to over 5000 registered users by the end of 2016 and produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware. The hacking agency is under the command of the CIA’s Center for Cyber Intelligence as seen in the image below. WikiLeaks compares this growth to the CIA creating its own version of the National Security Agency, but with even less management and accountability.
 The source of the leaks claims that the goal was to encourage public debate regarding the CIA’s hacking abilities and the larger issue of the security and creation of cyberweapons. “There is an extreme proliferation risk in the development of cyber ‘weapons’. Comparisons can be drawn between the uncontrolled proliferation of such ‘weapons’, which results from the inability to contain them combined with their high market value, and the global arms trade,” stated Julian Assange. “But the significance of “Year Zero” goes well beyond the choice between cyberwar and cyberpeace. The disclosure is also exceptional from a political, legal and forensic perspective.”
The source of the leaks claims that the goal was to encourage public debate regarding the CIA’s hacking abilities and the larger issue of the security and creation of cyberweapons. “There is an extreme proliferation risk in the development of cyber ‘weapons’. Comparisons can be drawn between the uncontrolled proliferation of such ‘weapons’, which results from the inability to contain them combined with their high market value, and the global arms trade,” stated Julian Assange. “But the significance of “Year Zero” goes well beyond the choice between cyberwar and cyberpeace. The disclosure is also exceptional from a political, legal and forensic perspective.”
The documents reveal that the hacking tools are built by EDG (Engineering Development Group), a software development group within the CCI. The EDG creates, tests, and offers support on all backdoors, exploits, trojans, viruses, and other malware used by the CIA in its surveillance operations. As part of a program code-named “Weeping Angel,” the CIA was able to target Samsung Smart TVs via a ‘Fake-Off’ mode which would deceive the owner into believing the TV is off. In this ‘Fake-Off’ mode the CIA could use the TV as a recording device for conversations in the room.
The CIA was also studying how to infect the vehicle control systems used by increasingly digital cars and trucks. The CIA’s Mobile Devices Branch (MDB) has also given the agency the ability to attack nearly all cell phones, specifically those created by Samsung and Apple. These infected phones can send the CIA the user’s location, audio recordings and text communication, in addition to secretly activating the microphone and camera. The MDB produced malware to infest, control and exfiltrate data from iPhones and other Apple products running iOS, such as iPads. Another unit targeted Google’s Android and developed 24 “weaponized” Android “zero days” which it has developed itself and obtained from GCHQ, NSA and cyber arms contractors.
CIA’s secret hacking division produced a huge amount of weaponized malware to infest iPhone. Android phones–and lost control of it. #Vault7 pic.twitter.com/KmFLEVmbnE
— WikiLeaks (@wikileaks) March 7, 2017
Another interesting piece of information from Vault 7, reveals that the CIA uses the U.S. consulate in Frankfurt as “a covert base for its hackers covering Europe, the Middle East and Africa.” Instructions for CIA hackers detail a lack of concern for security or being exposed. “Breeze through German Customs because you have your cover-for-action story down pat, and all they did was stamp your passport,” one document reads.
RFID Scan Blockers – Available for Free (Ad)
The documents also seem to indicate vulnerabilities in popular encrypted messaging platforms WhatsApp, Signal, Telegram, Wiebo, Confide, and Cloakman by hacking the “smart” phones that they run on and collecting audio and message traffic before encryption is applied. However, NSA whistleblower Edward Snowden tweeted, “PSA: This incorrectly implies CIA hacked these apps / encryption. But the docs show iOS/Android are what got hacked – a much bigger problem”. Snowden did seem to confirm that the documents were real. Snowden even offered a bit of advice to journalists digging through the documents.
If you’re writing about the CIA/@Wikileaks story, here’s the big deal: first public evidence USG secretly paying to keep US software unsafe. pic.twitter.com/kYi0NC2mOp
— Edward Snowden (@Snowden) March 7, 2017
The release of Vault 7 is yet further proof that the United States of America is now a real world representation of George Orwell’s infamous dystopian novel, 1984. The free hearts and minds of the world must resist this surveillance at every turn and stop participating in their own enslavement.
Derrick Broze is an investigative journalist and liberty activist. He is the Lead Investigative Reporter for ActivistPost.com and the founder of the TheConsciousResistance.com. Follow him on Twitter. Derrick is the author of three books: The Conscious Resistance: Reflections on Anarchy and Spirituality and Finding Freedom in an Age of Confusion, Vol. 1 and Finding Freedom in an Age of Confusion, Vol. 2
Derrick is available for interviews. Please contact Derrick@activistpost.com
This article may be freely reposted in part or in full with author attribution and source link.


It is so nice to have what we knew confirmed as the truth in writing!!!
Should the “Activist” part of A. Post express ideas about what we can do to begin rolling back the surveillance state? For instance, supporting the bipartisan Fourth Amendment Caucus and begin pushing back against all biometric tracking.
Continuous reporting not paired with context and calls for activism equate to normalizing and conditioning the rise of a police state….ironically predicated on the 9/11 False Flag attack – for which Wikileaks’ founder Assange states 9/11 Truth annoys him as a false conspiracy.
The rise of Big Brother is the *global Technocratic control grid*, not expressed in this article which limits the scope.
We the people have woken up, and no longer accept lies and illusions!
https://uploads.disquscdn.com/images/3dd6abb1966b02dde1639460a7742e99daf1f78da2dff4bbd6bd66d4ca01b07a.gif
Freedom of speech and freedom to privacy are fundamental human rights. Now that these rights have been removed by the corrupt PTB would it be fair to say that every man who died fighting to defend the freedom of future generations died in vain? Those with eyes that see and ears that hear will of course realise they died to increase the power of the oligarchs who have now created the surveillance system we are now all enslaved by.