 |
| Freda Art |
Eric Blair
A new report from the Department of Defense outlines the military’s capability to deter cyber threats with some pretty heavy firepower, including nuclear weapons.
The paper written by the Defense Science Board described the best types of bombs to use on hackers to be “Global selective strike systems e.g. penetrating bomber, submarines with long range cruise missiles, Conventional Prompt Global Strike (CPGS), survivable national and combatant command,” while “Nuclear weapons would remain the ultimate response and anchor the deterrence ladder” for cyber threats.
“The report … implies that the United States might have to rely on nuclear weapons to retaliate after a large-scale cyber attack,” Foreign Policy writes.
Although it seems that Foreign Policy is reporting shocking revelations, they’re actually engaged in subtle misinformation. They claim that this strike capability is only to be used in “retaliation” after a cyber attack as opposed to preemptive strikes to prevent cyber threats, which the military is already authorized to do.
For all the talk of the indefinite detention section of the National Defense Authorization Act (NDAA), a little known provision gave President Obama the authority to “conduct offensive operations in cyberspace”.
Here’s what Section 954 of the 2011 NDAA says:
SEC. 954. MILITARY ACTIVITIES IN CYBERSPACE.
Congress affirms that the Department of Defense has the capability, and upon direction by the President may conduct offensive operations in cyberspace to defend our Nation, Allies and interests, subject to—
(1) the policy principles and legal regimes that the Department follows for kinetic capabilities, including the law of armed conflict; and
(2) the War Powers Resolution (50 U.S.C. 1541 et seq.).
Prior to this NDAA provision, in July 2011, the Pentagon announced cyberspace to be their “operational domain” and claimed that the U.S. can “under the laws of armed conflict, respond to serious cyber attacks with a proportional and justified military response at the time and place of our choosing,” said Deputy Defense Secretary William Lynn during the release of The Department of Defense Strategy for Operating in Cyberspace.
 This week we heard Rand Paul speak much about the “law of armed conflict” or “Martial Law” in his talking filibuster of John Brennan over drone strikes on American soil, which is a related concern since the NDAA also officially labeled the U.S. as part of the battlefield.
This week we heard Rand Paul speak much about the “law of armed conflict” or “Martial Law” in his talking filibuster of John Brennan over drone strikes on American soil, which is a related concern since the NDAA also officially labeled the U.S. as part of the battlefield.
Paul reiterated that if Americans can be treated the same as an enemy under the law of armed conflict, there is no due process protection, as well as more flexible rules of engagement than those that restrict the police. Just ask the Guantanamo prisoners or Bradley Manning how due process works under the laws of war. Or ask the family of the 16-year-old American murdered by a targeted drone strike about the rules of engagement.
Therefore due process will not be needed to take offensive action against cyber threats under the laws of war. In other words, hackers everywhere may be facing a lethal force if they’re suspected of engaging in cyber attacks against the U.S. or its allies and interests.
The report, however, urges US military leaders to develop “cyber escalation scenarios and red lines” that could prompt the use of force. Or simply put, when can they pull the trigger on a cyber threat. Of course, just as the legal justification for drone strikes has remained classified, surely, this will as well.
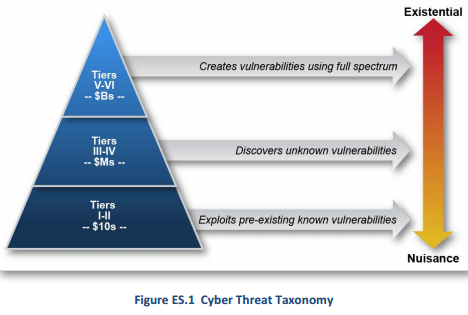
Here is a nifty illustration they provided to help us visualize how the threat levels are designed for hackers:
It’s also important to note that the military has been authorized to conduct a cyberwar with “kinetic capabilities”, meaning it can operate wherever the threat is in the world. A borderless war like the war on terror. This eliminates any need for the President to seek an individual declaration of cyber war against China in Congress even though nuclear weapons could potentially be involved.
Does anyone in Congress understand just how dangerous it is to authorize the use of preemptive deadly force against suspected cyber threats without due process?
Read other articles by Eric Blair Here


Be the first to comment on "DoD Plans to Use Preemptive Deadly Force on Hackers, Cyber Threats"