 |
| Dees Illustration |
Eric Blair
Activist Post
It was reported earlier this week that the FBI won a great victory by stopping the largest child porn distributor on the Internet. The FBI’s victory lap was cut short when some of the details of how they did it were more closely examined.
What the FBI actually did was seize a hosting service on the hidden TOR Network. The owner of the hosting service Freedom Hosting was not directly involved in the production or distribution of child porn, he just provided anonymous hosting used by pedophile pornographers.
The bigger question became how the FBI penetrated the supposedly anonymous TOR Network. That’s where the story gets interesting.
TOR, short for The Onion Router, was originally developed by the Navy Research Laboratory to provide an anonymous secondary internetwork for the government to use. Supposedly the project was abandoned by the Navy only to be picked up by open-source volunteers who now run the Tor Project.
Despite its beginnings as a government project, most believe TOR to be the best current option for online anonymity. But does this recent compromise of TOR reveal that it’s also part of the surveillance grid? The long answer is complicated, but the short answer is no.
First, the NSA has been identified as the source of the malware bomb used to take down Freedom Hosting – not the FBI who claimed victory in the investigation and apprehension.
Arstechnica writes:
Malware planted on the servers of Freedom Hosting—the “hidden service” hosting provider on the Tor anonymized network brought down late last week—may have de-anonymized visitors to the sites running on that service. This issue could send identifying information about site visitors to an Internet Protocol address that was hard-coded into the script the malware injected into browsers. And it appears the IP address in question belongs to the National Security Agency (NSA).
Continued from Arstechnica:
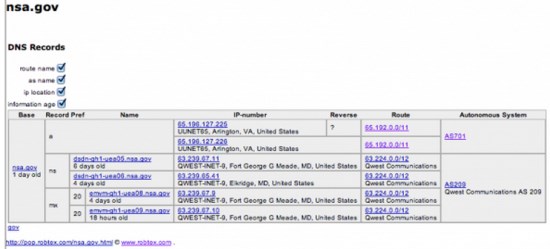
Initial investigations traced the address to defense contractor SAIC, which provides a wide range of information technology and C4ISR (Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance) support to the Department of Defense. The geolocation of the IP address corresponds to an SAIC facility in Arlington, Virginia.
Further analysis using a DNS record tool from Robtex found that the address was actually part of several blocks of IP addresses allocated by SAIC to the NSA. This immediately spooked the researchers.
 Two things are important to note about this revelation: First, it should be telling that the NSA had to resort to using a malware weapon instead of how they normally collect and decode Internet traffic — which still can’t be done on TOR; and, second, the open-source nature of TOR provided clear evidence of the breach and who caused it.
Two things are important to note about this revelation: First, it should be telling that the NSA had to resort to using a malware weapon instead of how they normally collect and decode Internet traffic — which still can’t be done on TOR; and, second, the open-source nature of TOR provided clear evidence of the breach and who caused it.
The TOR Project identified the specific problem and suggested that people who desire privacy must get the patched version of the TOR Browser Bundle, stop using Windows, and disable Javascript. If your Windows OS is compromised, which it clearly is, it doesn’t much matter how you sign in to the Internet. And, according to TOR, Javascript was used by the NSA to breach an older version of the TOR Browser Bundle.
Some feel this entire attack is more about scaring people away from using privacy tools such as TOR than it is about fighting child porn because no actual pornographers were caught. They remained anonymous. TOR is still considered secure if used properly.
But just as it was announced that the Drug Enforcement Agency was using warrantless NSA data to “investigate” drug crimes, it’s clear from this case that the FBI used NSA’s preemptive cyber attack on TOR for their own “investigation”.
Does anyone see a pattern of abuse forming yet? The government is illegally collecting, sharing and using our private data to drum up suspicion of criminal activity, and then acting on it.
They’re hoping headlines like “taking down the world’s largest child porn dealer” will justify crushing Internet freedom and privacy. Expect more victory laps by the FBI or DEA, and the NSA catching more “credible threats”. Keeping us safe, one privacy breach at a time.
Read other articles by Eric Blair Here


Be the first to comment on "NSA’s Cyber Army Attacks the Navy’s Tor Network, Gives Spoils to the FBI"